Cybercrime has risen significantly in the past few years, threatening not only your users’ data, but your platform’s stability as a whole. One particularly effective and damaging aspect of cybercrime is phishing, or the practice of sending deceptive messages designed to trick the recipient into revealing sensitive or personally identifying information. In 2020, the FBI’s Internet Crime Complaint Center received over 791,000 complaints, costing $4.2 billion in losses, with phishing attempts as the most frequently reported, and that number continues to grow. Furthermore, small businesses are especially vulnerable to phishing attempts, as they are often caught unprepared for the vast variety of attacks, and as of 2019, close to 43% of all cyberattacks now target small businesses.
The sophistication of computing has led to an improvement in the quality, scale, and speed of these attacks, and now phishing emails can look like innocent requests coming from your own colleagues, when in reality they can be coming from a hacker thousands of miles away. At Filestack, we’ve always emphasized the importance of security and phishing detection is yet another step we’ve taken to find and ultimately prevent vulnerabilities.
Filestack phishing detection within Workflows assists users with recognizing, handling, and removing malicious HTML, SVG, XML, and other kinds of files, protecting the integrity of their account. Users can quickly draft a low-code pathway that detects phishing files, and quarantine, delete, or run other processes on the file as they see fit using Workflows’ task-and-logic structure.
Filestack Phishing Detection
Filestack phishing detection is a post-processing method that occurs after a file has been uploaded. Running the detector will generate a Document Object Model (DOM) of the targeted file, which is a visualization of the document’s information so that the detector can analyze what it contains. Typically, phishing files will connect to servers used by hackers to store their scripts using external calls built into the file itself. Filestack phishing detection scans the file to find these connections between false login panels and these servers through a variety of proprietary methods on the DOM of the suspect file. This will let the user know if these calls to outside endpoints of phishing information exist within the uploaded file.
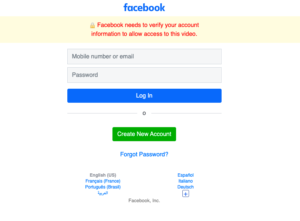
An example phishing file upload is below, which seems to be a simple request from Facebook for the viewer to login and watch a video. Note the misspelt or as o; grammatical or spelling errors can sometimes be markers of a phishing scam.
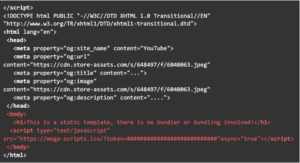
A portion of the document structure is below, where we see a call to a site that is clearly not a Facebook-based link marked in red. This is the external endpoint where the attacker’s scripts are, connected to the false login portion. The detector looks for these kinds of markers in its effort to flag a particular file as a phishing attempt or not.
Advanced phishing detection is entirely and solely a part of the Filestack Workflows low-code configuration toolkit. Workflows is a simple low-code GUI that simplifies the user’s experience so they can tap into vast capabilities of the Filestack API, such as sentiment analysis, video tagging, or virus detection. Users can create a logic for each one of their file uploads, handling them as they see fit using Workflows’ straightforward “click-and-drag” visualization of file ingestion pathways. Read more about what you can achieve with Workflows here.
Closing Thoughts
Phishing is a major problem for any company or individual to deal with. What seems to be just a message sent by someone you know can actually turn out to be sinister attempts to steal your important information, and cripple your infrastructure. Building your own phishing detector can be a challenging task, necessitating a heavy workload on your development team to constantly update the detector to fit the ever-improving quality of phishing. The Filestack phishing detection algorithm gives you the tools you need to achieve the protection of your company, your customers, and their information, wrapped up in the easy-to-use low-code Workflows configuration tool.
Try Filestack today – signup for a free account
Filestack is a dynamic team dedicated to revolutionizing file uploads and management for web and mobile applications. Our user-friendly API seamlessly integrates with major cloud services, offering developers a reliable and efficient file handling experience.
Read More →