How is your application’s file upload security? Filestack provides secure file upload features that can be included in any application, protecting the platform’s upload gateway. In addition to this, the Filestack API is protected through parameters like custom API keys, domain whitelisting and Filestack Policies and Signatures. Here’s what you need to know about the ways Filestack protects its upload processes.
Domain Whitelisting Features
Your front-end uses an API key to connect to your Filestack resources. Domain whitelisting ensures that an API key can only be used when set on certain domains (a regular expression can be used to create a list of domains). No one else will be able to use your API key; domain whitelisting eliminates the worry of API key exposure.
Without domain whitelisting, it’s possible for someone else to potentially freeload off your API key and use up your Filestack resources. Of course, domain whitelisting is only one of the necessary application security features. It only prevents someone else from using your resources, and may not protect from more malicious attacks. Therefore, it should be used in addition with other Filestack security solutions.
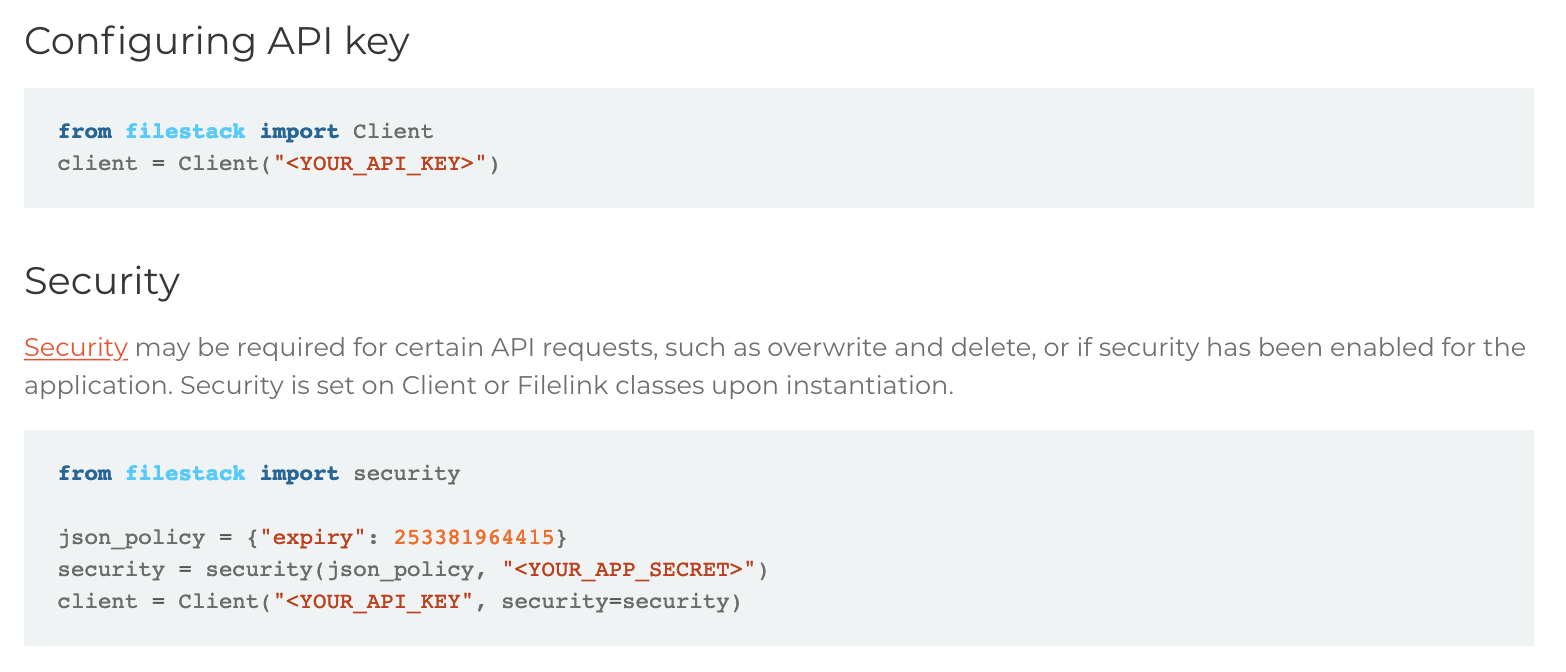
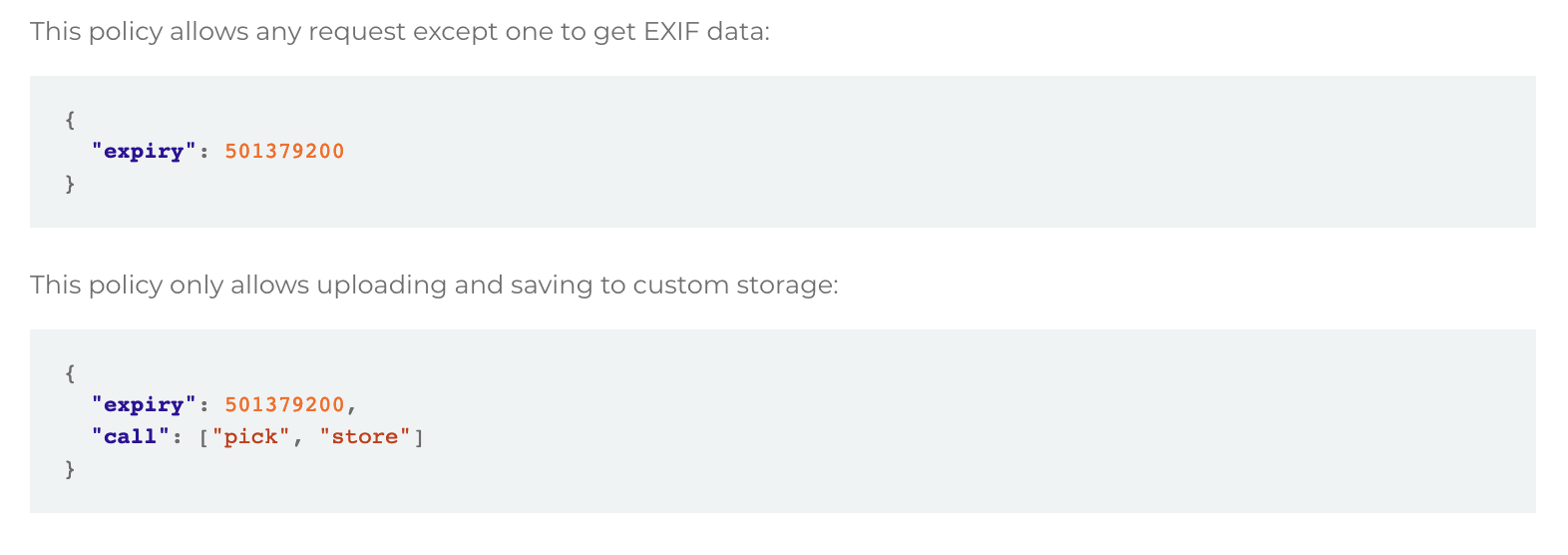
Policies and Signatures
Policies and signatures are used to determine a file upload’s destination, and it can be changed without security parameters. Policies and signatures are given during site rendering but with an expiry period, and can be used to protect the application by expiring unused requests in a timely manner. The management of policies is important to make sure that the system isn’t exposed to any unnecessary risk.
Encoding and Encryption
Both encoding and encryption provide an additional layer of security to the Filestack upload process. Encoding turns human readable information into the correct format of computer readable data, while encryption makes it so that the data cannot be read without the proper key. Even if someone else is able to acquire an encrypted file or encrypted data, they won’t be able to read it. Encrypting data as it is transferred is important and should be front of mind to avoid hijacked or compromised data.
As a general rule, anything that can be encrypted should be encrypted. Filestack additionally uses SSL to encrypt data that is coming to and from the program, even if the connection itself isn’t secure (such as public WiFi). Encryption protocols are a must have security standard.
The Standard Features of Filestack
Filestack comes standard with encryption, secured transfers and secured storage. Additionally, Filestack provides access control over these encrypted files with authentication and authorization processes intended to restrict access to only the user accounts that need the data.
Network isolation protects the rest of the application from uploaded files, in addition to security policies and exif data checking. When files are initially uploaded, they are kept separate from the rest of the network, even before being scanned. If there are any sort of malicious programs detected, they can be addressed and mitigated without putting the rest of the application at risk.
A privacy shield and GDPR support also improve upon the download’s security and privacy management processes, which is now necessary for the purposes of regulatory compliance. Privacy has become an important issue when it comes to file uploads, as many documents may include personally identifiable information that could expose the user to risk.
The Importance of Application Security
Filestack’s complete application security protects the upload gateways of an application, not only securing the Filestack process but also securing data once it has been entered into the Filestack platform. Application security is critical to any platform, as otherwise all users could find themselves being exposed to threats.
Through Filestack, a platform is able to acquire best-in-class upload and download security features without having to manage or create them on their own. Instead of having to reinvent the wheel, users are able to drop-in features and connect to them using a unique API key. At the same time, this functionality must also be secured. If the API key and the domain aren’t protected, then someone else may be able to use the Filestack resources associated with an application.
To that end, Filestack provides its own level of security that comes in the form of encryption, encoding, policies and other methods of security management. To learn more, you can reference the extensive documentation available around securing your application.
As a secure document upload API, Filestack can be used to protect your application and its users from potentially malicious programs. To explore the benefits of Filestack, sign up for free today!
Filestack is a dynamic team dedicated to revolutionizing file uploads and management for web and mobile applications. Our user-friendly API seamlessly integrates with major cloud services, offering developers a reliable and efficient file handling experience.
Read More →