Uploading files using PHP seems simple—until it isn’t. What starts as a basic script can quickly become a nightmare of security vulnerabilities, server crashes, and corrupted files if not handled properly. Whether you’re building a portfolio upload form or handling client documents in a web app, file uploads are one of the most exploited entry points in any PHP-based system.
That’s why understanding what not to do is just as important as knowing how to build a PHP file upload script.
In this article, we’ll explore the top 6 mistakes developers make when handling file uploads in PHP—and how to avoid them.
Key takeaways
- Validating file types is critical to prevent attackers from uploading malicious scripts disguised as safe files.
- Setting file size limits at both the server and script level avoids server crashes and storage overload.
- Always check for file upload errors using $_FILES[‘error’] to catch partial or failed uploads.
- Rename uploaded files to prevent accidental overwrites and ensure safe, unique file storage.
- Avoid exposing files to the public—store them securely and serve via controlled access or use platforms like Filestack.
1. Not validating file types
One of the most common (and dangerous) mistakes in a PHP file upload script is failing to validate file types. Without proper checks, your application becomes a playground for attackers who can upload malicious files—like .php, .exe, or .sh—disguised as harmless uploads.
Why it matters:
If an attacker uploads a PHP script and manages to execute it on your server, they could gain unauthorized access, steal data, or take control of your system. Even innocent-looking files like .jpg can be embedded with dangerous code if not validated correctly.
Example:
Imagine your script accepts all file types without restriction. A user uploads a file named shell.php, which contains harmful code. If the file is stored in a publicly accessible folder and executed, your entire application could be compromised.
How to fix it:
Instead of relying solely on the file extension (which can be easily faked), validate the MIME type using PHP’s mime_content_type() or finfo_file() function. Always maintain a whitelist of acceptable MIME types based on your use case.
Here’s a sample file validation in PHP:
$allowedTypes = ['image/jpeg', 'image/png', 'application/pdf'];
$fileMimeType = mime_content_type($_FILES['upload']['tmp_name']);
if (!in_array($fileMimeType, $allowedTypes)) {
die('Error: Invalid file type.');
}
Pro tip:
You can also check the file extension in combination with the MIME type for added security—but never rely on the extension alone.
2. Missing file size limits
Failing to enforce the PHP file upload size limit is a recipe for disaster—especially on shared hosting environments or resource-constrained servers. Without proper restrictions, users (or bots) could upload massive files that consume memory, fill up disk space, or crash your PHP application entirely.
Why it matters:
Imagine someone uploads a 2GB video file when your server is only configured to handle files under 100MB. The result? Your application slows down, times out, or even crashes—leading to a poor user experience or potential downtime.
How to fix it:
There are two levels where you should enforce file size limits:
1. Server-side (php.ini settings):
Edit your php.ini file and configure these directives:
upload_max_filesize = 10M
post_max_size = 12MThese control the maximum size of individual uploads and the total POST request size.
2. Script-level validation in PHP:
Even with server settings in place, always double-check the file size in your PHP script using:
$maxSize = 10 * 1024 * 1024; // 10MB in bytes
if ($_FILES['upload']['size'] > $maxSize) {
die('Error: File size exceeds the allowed limit.');
}
Bonus UX Tip:
Always inform users about file size limits up front on your upload form. This helps avoid frustration and failed uploads. Example:
<small>Max upload size: 10MB</small>3. Not checking for upload errors
A common oversight in many PHP file upload scripts is skipping proper error checks after a file upload attempt. Developers often assume that if $_FILES is populated, the upload was successful—but that’s not always true.
Why it matters:
PHP provides a built-in mechanism to detect what went wrong during the upload process using $_FILES[‘your_input_name’][‘error’]. Ignoring this check can result in broken files, incomplete uploads, or even silent failures.
Understanding $_FILES[‘error’] values:
| Value | Meaning |
| 0 | No error, upload successful |
| 1 | File exceeds upload_max_filesize |
| 2 | File exceeds MAX_FILE_SIZE in HTML |
| 3 | File only partially uploaded |
| 4 | No file was uploaded |
| 6 | Missing temporary folder |
| 7 | Failed to write file to disk |
| 8 | A PHP extension stopped the upload |
Each code gives insight into what went wrong—and how you can handle it more gracefully.
Mistake: Assuming the upload is always successful
Without checking the error status, you might move or store a file that didn’t even upload properly.
How to fix it: Add proper PHP file upload error handling like this:
if ($_FILES['upload']['error'] !== UPLOAD_ERR_OK) {
die('Upload failed with error code: ' . $_FILES['upload']['error']);
}
Pro Tip:
Use a switch statement or a helper function to return user-friendly error messages based on the error code for better debugging and UX.
4. Saving files without renaming
Another major mistake in a PHP file upload script is saving uploaded files with their original filenames. While this may seem convenient, it opens the door to serious issues like overwriting existing files or causing naming conflicts between users.
The problem:
If multiple users upload files with the same name (e.g., resume.pdf), the newer upload can overwrite the previous one—especially if all uploads go to the same directory.
The risk:
This can result in user data loss, accidental overwriting of sensitive configuration files, or even security vulnerabilities if executable files are uploaded and stored carelessly.
How to fix it:
Always rename uploaded files before saving them to your server. A good approach is to use unique identifiers like uniqid() or generate a hash of the original filename combined with a timestamp.
Example using uniqid():
$originalName = $_FILES['upload']['name'];
$extension = pathinfo($originalName, PATHINFO_EXTENSION);
$newFileName = uniqid('upload_', true) . '.' . $extension;
$uploadPath = 'uploads/' . $newFileName;
move_uploaded_file($_FILES['upload']['tmp_name'], $uploadPath);This way, even if two users upload files named invoice.pdf, they’ll be saved with unique names, eliminating conflicts.
5. Skipping server-side file validation
Relying solely on client-side validation (such as JavaScript) is a risky approach when handling file uploads in PHP. While front-end checks may improve the user experience, they can be easily bypassed—especially by attackers using tools like Postman or custom scripts.
The problem:
If you don’t validate files on the server, users could upload unsupported file types, oversized files, or even malicious content. This not only breaks your upload logic but also puts your entire application at risk.
Why it matters:
Server-side validation ensures that only safe and expected files get processed—even if client-side rules are ignored. Skipping this step can lead to security breaches, data corruption, and poor application stability.
What to validate server-side:
- File type (MIME type)
- File size
- File extension
- File upload success ($_FILES[‘error’])
- Storage location and name
Here’s a basic PHP server-side validation example:
$allowedTypes = ['image/jpeg', 'image/png', 'application/pdf'];
$maxSize = 5 * 1024 * 1024; // 5MB
$file = $_FILES['upload'];
if ($file['error'] !== UPLOAD_ERR_OK) {
die('Upload failed.');
}
if (!in_array(mime_content_type($file['tmp_name']), $allowedTypes)) {
die('Invalid file type.');
}
if ($file['size'] > $maxSize) {
die('File too large.');
}
Pro Tip:
For even stronger validation, consider scanning uploaded files using antivirus APIs or sandboxing tools—especially if your app handles user-generated content.
6. Storing files in publicly accessible folders
Many developers make the mistake of saving uploaded files directly into public folders like /uploads/, which can be accessed by anyone with a direct URL. While it might seem like an easy way to serve files, it poses a major security risk—especially if users can upload executable files.
The problem:
If a malicious user uploads a .php, .sh, or any executable script and it’s stored in a publicly accessible directory, it could be executed directly in the browser. This could lead to server hijacking, data theft, or even full system compromise.
Example:
Let’s say someone uploads evil.php to your /uploads/ folder. If that folder is public, they could simply go to yourdomain.com/uploads/evil.php and trigger the script.
How to fix it:
- Store uploads outside the web root:
Instead of putting files in /public/uploads/, place them in a non-public directory like /var/www/uploads/. Then serve them through a controlled script that validates access.
2. Use .htaccess or server rules to block execution:
If you must store files inside a public directory, create a .htaccess file to block access to scripts:
<FilesMatch "\.(php|exe|sh)$">
Deny from all
</FilesMatch>
- Restrict download access through token-based or role-based access logic.
Bonus tip:
Rename all uploaded files and strip out dangerous extensions—even if you already perform MIME type checks.
Extra security tip: always use HTTPS
Even the most secure PHP file upload script can be compromised if the connection between the client and server isn’t encrypted. That’s why using HTTPS is not optional—it’s essential.
The threat:
When users upload files over an unencrypted HTTP connection, the data is sent in plain text. This makes it vulnerable to man-in-the-middle (MITM) attacks, where attackers intercept and possibly alter the file before it reaches your server.
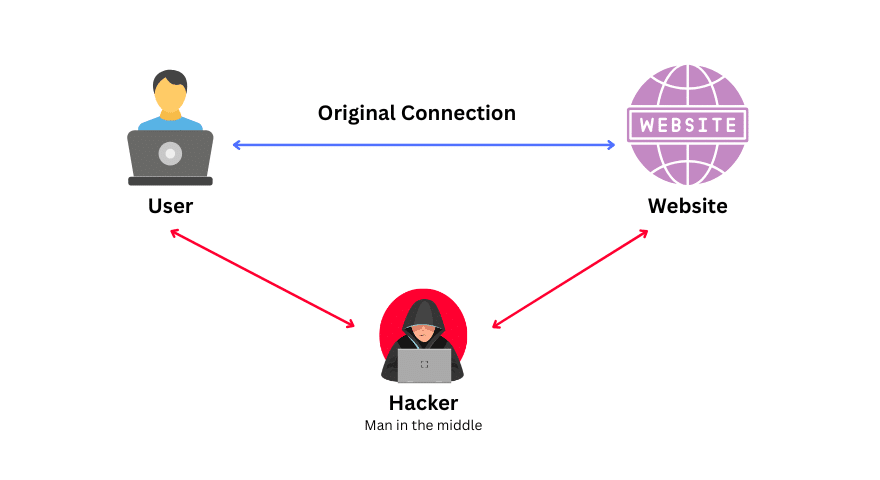
The fix:
Always serve your site over HTTPS using a valid SSL certificate. This ensures that all data—including uploaded files—is transmitted securely and cannot be intercepted or tampered with during transit.
Why it matters:
Even if your upload logic is perfect, failing to use HTTPS creates a gaping hole in your security. Without it, users’ files (and potentially sensitive data) could be exposed during upload.
Bonus tip:
Let’s Encrypt offers free SSL certificates, making it easy for developers to secure their websites without added cost.
Learn more in the PHP official documentation.
Get the full example PHP file upload script from this GitHub repository.
Filestack PHP file upload
If you’re looking for a secure, scalable, and developer-friendly way to handle file uploads in PHP, Filestack makes it easy.
Instead of worrying about validating file types, setting size limits, renaming files, handling errors, or configuring secure storage manually, Filestack takes care of all the heavy lifting. Their platform comes with built-in security features, automatic virus detection, intelligent file transformations, and seamless CDN delivery.
Why use Filestack?
Filestack helps you avoid many of the mistakes discussed in this article by:
- Enforcing file type and size restrictions
- Handling error messages and upload logic internally
- Automatically renaming files to prevent collisions
- Storing uploads securely in the cloud
- Serving all files over HTTPS
Filestack PHP file upload example
Here’s a basic example of how to upload a file using the Filestack PHP SDK:
Step 1: Install the Filestack PHP SDK via Composer
composer require filestack/filestack-phpStep 2: Use the SDK in your script
// Include the Composer autoload file
require_once 'vendor/autoload.php';
use Filestack\FilestackClient;
// Replace with your actual Filestack API Key
$apiKey = 'YOUR_API_KEY';
// Initialize Filestack Client
$client = new FilestackClient($apiKey);
// Upload a local file (you can adjust the path as needed)
$result = $client->upload([
'filepath' => '/path/to/your/file.jpg',
]);
// Output the uploaded file URL
echo 'Uploaded File URL: ' . $result->url();Pro Tip: You can configure file type filters, max file size, and storage options directly from your Filestack Developer Portal.
If you’re serious about secure file uploading in PHP, Filestack provides a modern alternative to writing and maintaining complex upload scripts from scratch.
Get the complete example of a secure Filestack PHP file upload from this GitHub repository.
Explore more in Filestack’s comprehensive documentation.
Conclusion
Handling file uploads in PHP might seem simple, but small mistakes can lead to big problems—from security risks to broken user experiences.
To recap, avoid these six common pitfalls:
- Not validating file types
- Missing size limits
- Skipping error checks
- Not renaming files
- Ignoring server-side validation
- Storing files in public folders
By fixing these issues early, you can make your upload script more secure, reliable, and user-friendly. Or, if you prefer a hassle-free solution, try Filestack—it handles uploads the right way, out of the box.
FAQs
1. Why should I validate file types in a PHP file upload script?
Validating file types prevents malicious files—like disguised PHP scripts or executables—from being uploaded. Use MIME type checks along with file extension validation for better security.
2. How can I limit file upload sizes in PHP?
You can limit file size by setting upload_max_filesize and post_max_size in your php.ini. Also, check the $_FILES[‘file’][‘size’] value in your PHP script to enforce server-side size limits.
3. What does $_FILES[‘error’] mean in PHP uploads?
The $_FILES[‘error’] value shows the status of the upload. Always check it to detect issues like incomplete uploads, file size violations, or missing files.
4. Is it safe to keep original file names in uploads?
No. Original file names can cause conflicts or security risks. Rename uploaded files using uniqid() or UUIDs to avoid collisions and reduce exposure to injection attacks.
5. How does Filestack simplify PHP file uploads?
Filestack provides a modern file upload solution with built-in security, CDN delivery, and SDKs. It removes the need for writing custom validation, file renaming, or handling storage complexities.
Shamal is a seasoned Software Consultant, Digital Marketing & SEO Strategist, and educator with extensive hands-on experience in the latest web technologies and development. He is also an accomplished blog orchestrator, author, and editor. Shamal holds an MBA from London Metropolitan University, a Graduate Diploma in IT from the British Computer Society, and a professional certification from the Australian Computer Society.
Read More →

