File upload support is an integral part of many apps and software. Users need to upload files for archiving, submitting data, sharing content, exchanging digital pictures, and more tasks. However, uploading different types of files can pose risks and make your system open to different types of hacks and attacks. All developers need to be aware of file upload vulnerability, its causes and consequences, and how to prevent these vulnerabilities.
In this detailed guide, we’ll discuss various aspects of file vulnerability. We’ll also explain how you can use a third-party solution to prevent these vulnerabilities and make your system secure. Whether you are looking for a Java, Javascript, React, Ruby, Angular, or Python file upload, Filestack offers a great solution. You can avail Filestack services for uploading files securely and reliably.
What Is File Upload Vulnerability?
Just as the name suggests, the term “file upload vulnerability” implies the risks or dangers posed by uploading files to a website, server, or app. Hackers or attackers who want to take over your system or abrupt your system’s services, upload files that contain malicious code. Once uploaded, they can find a way to execute this code.
If you allow unchecked and unverified file uploads, you expose your system to possible dangers and attacks. All types of files, including spreadsheets, documents, pdfs, and more, can pose a risk if you do not validate file uploads. Even image files can contain malicious code that can harm your system.
What Are The Possible Consequences Of File Upload Vulnerability?
File upload vulnerability can lead to serious and dangerous consequences. For example, some of them are:
- An attacker can overwrite important files necessary for the correct functioning of your system. If you do not place restrictions on file uploads, hackers can even overwrite server-side files. This can give them access to your entire system and bring down an entire website or service.
- An attacker can initiate a denial of service (DoS) attack by uploading extremely large files to your system in parallel. This will make the server busy with file uploads, and it will start refusing requests from your genuine users.
- A hacker or attacker can upload a file containing malicious executable code. The malicious code can overwrite a system’s security setting, delete existing critical files and data, access important users’ data, and even disrupt the regular services of the system.
- If you allow unchecked file uploads, it can lead to a client-side attack involving a cross site scripting (XSS) attack.
- An attacker can use your server or system to store illegal content or software if you allow unchecked file uploads.
What Are The Causes Of File Upload Vulnerabilities?
Various factors lead to file upload vulnerability, making your system viable to different types of attacks. For example, some of these reasons are:
- If you do not restrict the type of file a user uploads, it can make your system vulnerable to attacks. For example, allowing the uploads of files with extensions .exe, .cmd, .js, and more can lead to dangerous consequences. Moreover, if file types are not properly checked, for example, only the lower case version is checked and not the upper case, then again this can lead to problems.
- If you do not restrict the size of the file that a user uploads, attackers can initiate a denial of service attack. They can start uploading many large files to your system simultaneously, which can choke the system, making it unable to perform routine tasks. Also, this can lead to the failure to process requests by other genuine users.
- If you allow your users to upload files to a server’s directory, then an attacker can easily overwrite some of the critical system files. If you do not have separate directories for admin and user files, you are making your system vulnerable. A separate public folder, where all users can upload files, is essential for a secure system. Moreover, all important critical files should be in password-protected directories, which can only be accessed by admin users.
- Transferring files through insecure channels.
- If you do not encrypt files when uploading them, then it can also cause problems. For example, a file containing important data, such as credit card information, personal data, and more, can easily fall into the hands of an eavesdropper.
- Outdated anti-virus software on your system can also make it vulnerable to attacks.
How Can I Prevent File Upload Vulnerabilities?
A great way of preventing file uploading vulnerabilities is to use an off-the-shelf solution. This is an easy and quick method to enable security in your system. Also, it does not require much effort on your part. Some benefits of using a third-party solution include:
- You can get enterprise-grade security of your system.
- The file upload services generally use up-to-date anti-virus software to make sure no malicious code can enter your system.
- There are easy-to-use APIs or JavaScript libraries for file uploads that you can integrate into your software’s front-end and back-end.
- The file upload routines are tried and tested by a third party. You can rest assured that you have a reliable and robust method of supporting file uploads to your users.
Why Should I Opt For Filestack To Prevent File Upload Vulnerabilities?
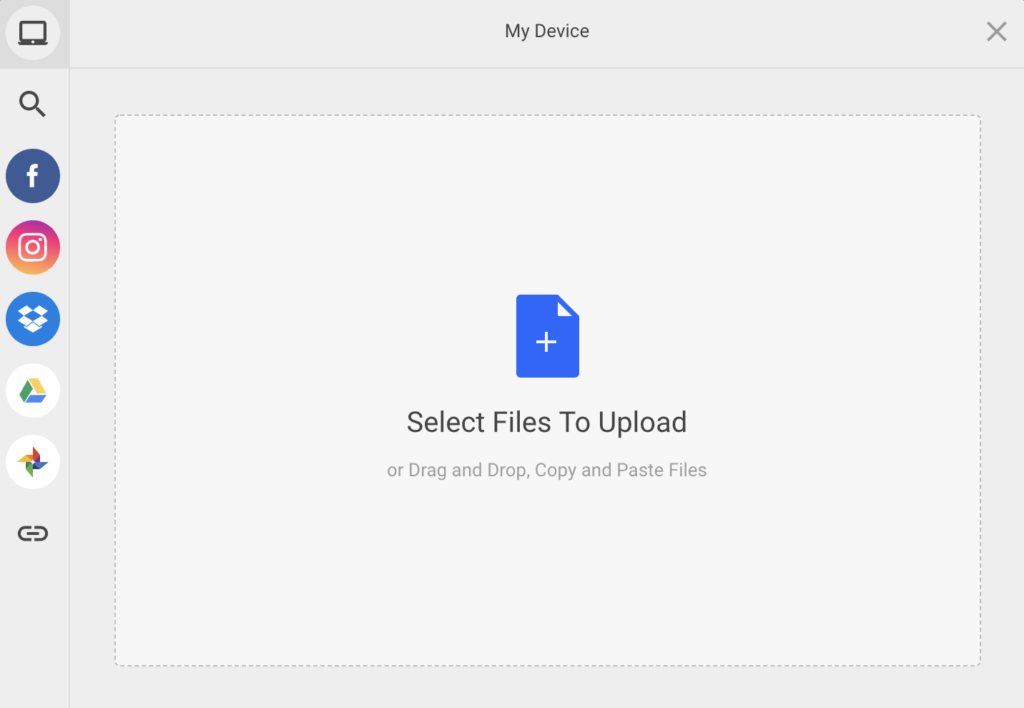
If you are looking for a fast, robust and secure file upload service, then Filestack is the right answer to all your needs. It makes files access easy and reliable. Additionally, you can use Filestack to enhance a user’s file uploading experience in a web app. Filestack offers numerous ways of uploading files. For example, you can do basic uploads, multipart uploads, cloud uploads, and more. Moreover, using Filestack APIs or SDK, you can also enable file uploads in a web form or use drag-and-drop. You can even copy and paste files. Additionally, Filestack maintains integrations with many popular services so it requires no integration effort from your side.
So what are you waiting for? Sign up for free and get the best file uploading service with Filestack!
Filestack is a dynamic team dedicated to revolutionizing file uploads and management for web and mobile applications. Our user-friendly API seamlessly integrates with major cloud services, offering developers a reliable and efficient file handling experience.
Read More →