As cyber threats are increasing exponentially, the need for secure file delivery is more pressing than ever. It helps protect sensitive data from unauthorized access, interception, and tampering. This builds trust with users and clients and prevents financial losses and operational disruptions. Moreover, depending on the industry and country you are operating in, you may have to comply with regulatory requirements concerning data privacy and security, such as GDPR and HIPAA. Secure file delivery helps organizations comply with these regulations.
Secure file delivery includes protecting files during transfer as well as while they are stored. It involves various techniques and mechanisms like encryption, secure file transfer protocol, authentication, access control, and more. Moreover, you can also use a reliable and secure file delivery platform like Filestack.
Filestack implements robust security features, such as end-to-end encryption, advanced authentication and authorization mechanisms, and more.
In this article, we’ll focus on:
- Security measures, encryption techniques, access control mechanisms, and best practices for secure transfer and storage of sensitive files.
- Implementing secure file delivery using Filestack’s platform.
Secure File Delivery with Filestack
Filestack is a powerful file management solution offering a complete set of powerful tools and APIs for:
- Secure file uploads
- Transformation
- Secure online file delivery
- Intelligence services, such as OCR, image tagging, facial detection, and more
File Upload and Delivery
Filestack provides a fast, secure, and highly efficient file uploader called the File Picker. Implementing the uploader requires just a few lines of code and you can also customize it, depending on your requirements.
In addition to file uploads from local devices, Filestack file uploader supports file uploads from various other sources, including Dropbox, Facebook, Google Drive, Google Photos, Instagram, and more.
Filestack supports quick and secure file delivery through a reliable CDN. After a file is uploaded via the Filestack File Picker, a CDN URL is instantly provided. This URL can be used for direct file delivery or for applying transformations through the Filestack Processing API before delivery.
Setting Up Secure File Delivery with Filestack
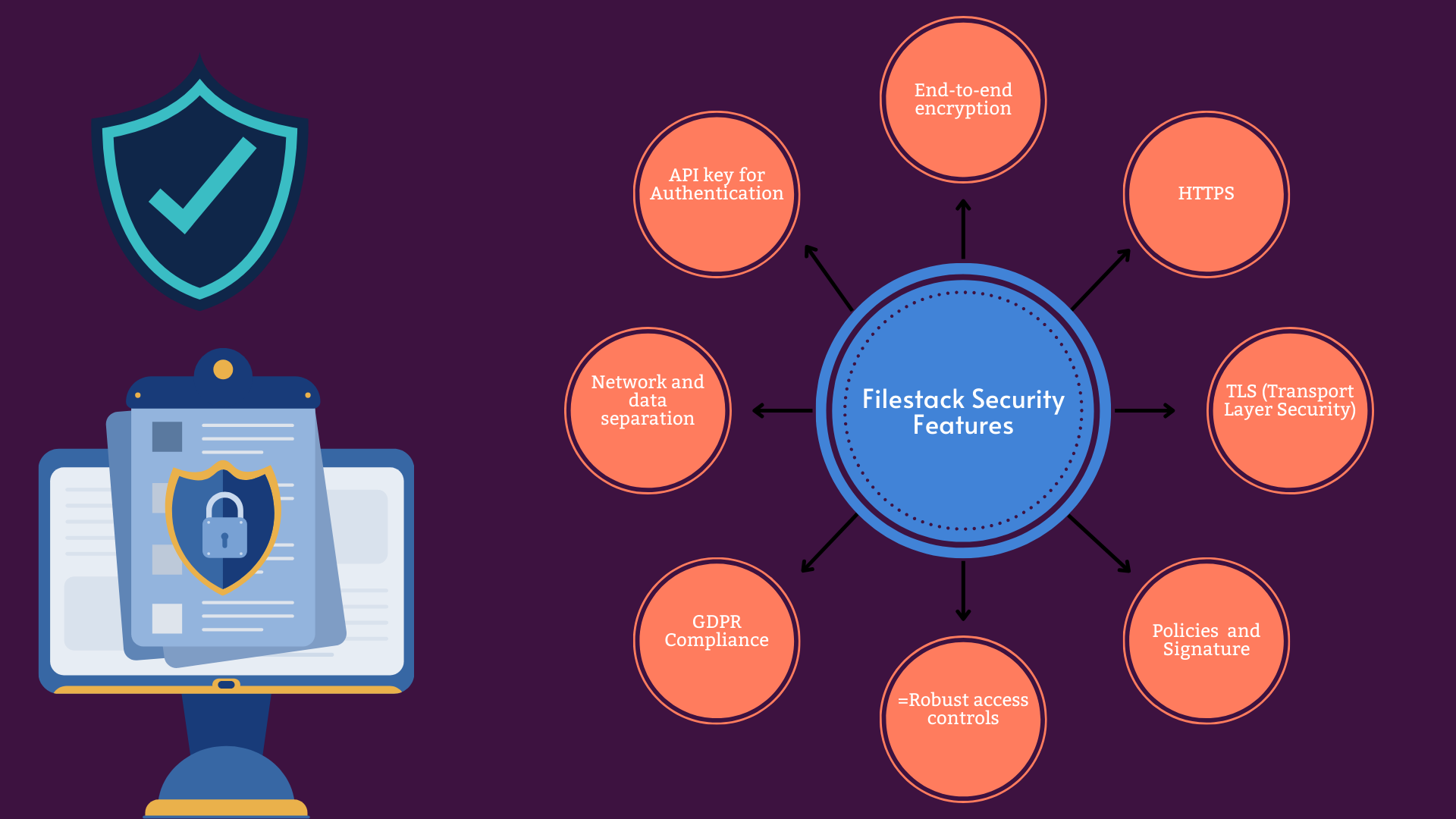
Filestack is a secure file transfer solution offering the following prominent security features:
End-to-end encryption
Filestack implements end-to-end encryption (E2EE) to ensure all the files and user data are highly protected. E2EE ensures that data remains encrypted throughout its entire file transfer lifecycle. This includes upload, processing, and storage. This encrypted file transfer means Filestack protects your files even when they are sitting idle on your server.
Filestack also allows you to integrate the file uploader with a cloud service of your choice such as AWS, and Google Drive. You can choose a secure cloud storage solution that implements strong encryption mechanisms to ensure your files are protected while they are stored.
Hypertext Transfer Protocol
Filestack employs HTTPS to ensure that all data transmitted between the client and Filestack’s servers is encrypted. This protects sensitive information, such as user data and uploaded files, during transmission.
TLS (Transport Layer Security)
Filestack also uses Transport Layer Security (TLS) as it provides an effective way to secure all communications between two points. Thus, TLS helps prevent malicious file upload problems.
Authentication and Authorization
Filestack employs advanced authentication and authorization mechanisms for API calls. This ensures secure access to Filestack services.
Filestack requires every developer to obtain a unique API key to authorize access to Filestack services.
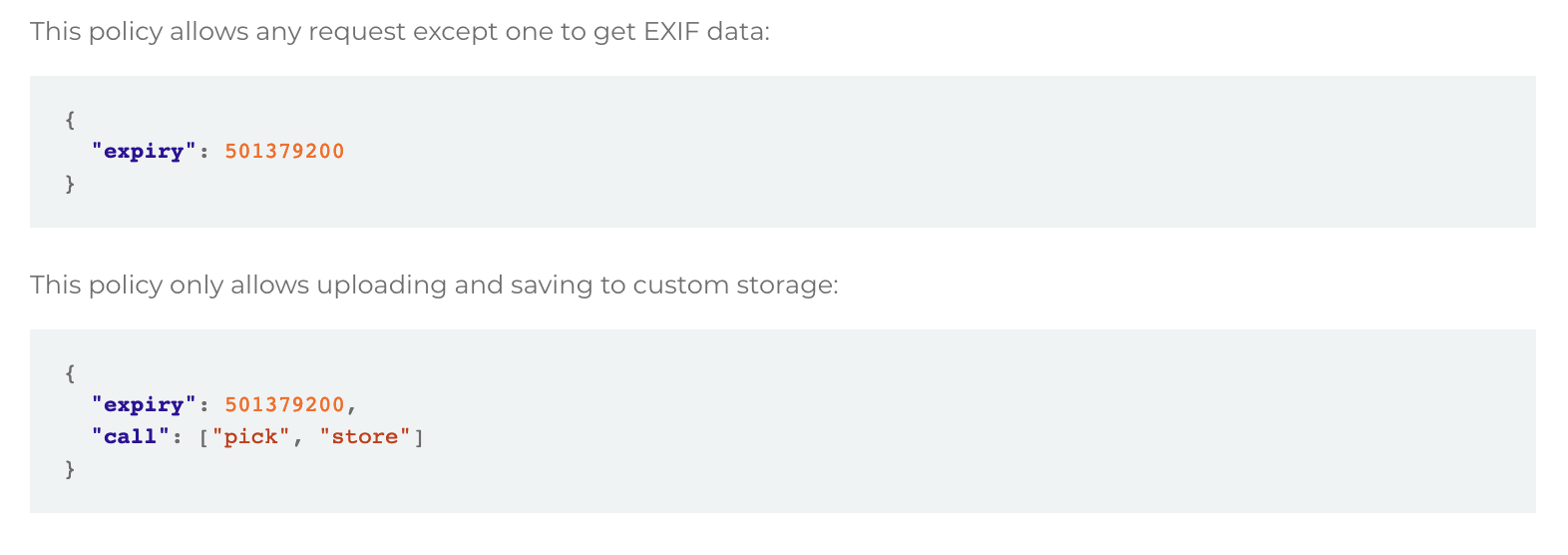
Moreover, authentication and authorization against Filestack APIs rely heavily on JSON “policies” (Base64URL-encoded) and HMAC-SHA256 “signatures”. Policies and Signatures help identify which actions are authorized and which are not.
Additionally, policies and signatures have an expiry period. This means you can expire unused requests for data security and protection.
Robust access controls
Filestack also utilizes powerful access controls, ensuring highly secure file transfers. You can control exactly who can see and use specific information, right down to individual user accounts. Additionally, you can monitor what each person does within the system. This helps you understand why changes are made and who is responsible for those changes.
General Data Protection Regulation/GDPR Compliant file transfer
Filestack complies with GDPR, a regulation focusing on protecting the privacy and personal data of individuals. This means Filestack follows strict rules and practices to ensure that personal data is handled securely and responsibly.
Network and data separation
Filestack provides an additional layer of security with network isolation. This means even if a cybercriminal somehow gains access to the network, zoning will be in place. This zoning or segmentation will provide the controls required to limit malicious activities during intrusion.
Code Snippet: Initializing Filestack with Secure Configurations
First, integrate the Filestack File Picker into your web app:
<script src="//static.filestackapi.com/filestack-js/3.x.x/filestack.min.js"></script>Configure the client with your API Key:
const client = filestack.init(YOUR_API_KEY);
client.picker().open();Make sure you’ve enabled E2E, set up role-based access control, etc.
Implementing Encrypted File Transfers
Encryption is one of the most efficient ways to protect your files and data during transfer and at rest. This includes both client-side and server-side encryption.
Client-side encryption involves encrypting files before they are uploaded to the server. This ensures that the data remains secure during transmission and storage.
Client-side encryption involves techniques like end-to-end file encryption. To make the encryption more robust, you can also use algorithms like AES (Advanced Encryption Standard)to encrypt and decrypt the file with the same key. Moreover, implementing secure key management practices is crucial. It helps protect encryption keys and prevent unauthorized access to encrypted data.
Server-side encryption involves encrypting files once they are uploaded to the server. The server manages the encryption keys as well as the encryption/decryption processes.
Example Code Snippets
Here is an example of implementing client-side encryption using the AES algorithm and Web Crypto API in JavaScript:
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Client-Side Encryption</title>
</head>
<body>
<input type="file" id="fileInput">
<button onclick="uploadFile()">Upload File</button>
<script>
async function generateKey() {
return crypto.subtle.generateKey(
{
name: "AES-GCM",
length: 256,
},
true,
["encrypt", "decrypt"]
);
}
async function encryptFile(file, key) {
const iv = crypto.getRandomValues(new Uint8Array(12));
const plaintext = await file.arrayBuffer();
const ciphertext = await crypto.subtle.encrypt(
{
name: "AES-GCM",
iv: iv
},
key,
plaintext
);
return { ciphertext, iv };
}
async function uploadFile() {
const fileInput = document.getElementById('fileInput');
if (fileInput.files.length === 0) {
alert('Please select a file to upload.');
return;
}
const file = fileInput.files[0];
const key = await generateKey();
const { ciphertext, iv } = await encryptFile(file, key);
const formData = new FormData();
formData.append('file', new Blob([ciphertext]));
formData.append('iv', new Blob([iv]));
formData.append('key', await crypto.subtle.exportKey('jwk', key));
fetch('/upload', {
method: 'POST',
body: formData
})
.then(response => response.json())
.then(data => console.log('File uploaded successfully:', data))
.catch(error => console.error('File upload error:', error));
}
</script>
</body>
</html>
If you are using Filestack for secure file transfer, you can simply enable E2EE through your Filestack account.
Access Control Mechanisms
File access control mechanisms ensure that only authorized users can access specific files or perform certain actions. In other words, you can control who can access files and what they can do with them. There are multiple ways to do this:
Setting Up User Authentication for File Access
With user authentication, you can verify the identity of users trying to access your system/files.
Effective File Delivery authentication methods include:
- Implement Username and Password: Users must log in using a combination of username and password.
- OAuth: Authenticate users through third-party services, such as Google or Facebook.
- Multi-Factor Authentication (MFA): Multi-factor authentication for files adds an extra layer of security. It requires users to provide two or more forms of verification to access an account or system. This means even if an unauthorized user knows the password, they can’t access the account.
Implementing Role-Based Access Control
Role-Based Access Control (RBAC) makes it easy to manage access rights. It ensures that users only have access to the resources/files they require. RBAC involves defining roles and permissions:
- Roles: Define roles such as Admin, User, and Guest.
- Permissions: Assign specific permissions to each role, such as read-only, write, and delete.
Time-Limited Access Tokens
With time-limited access tokens, we can provide temporary access to files. This way, a user or app can access sensitive data for a limited time, enhancing security.
Here are some ways to implement token expiry:
- Use tokens that expire quickly, such as after 15 minutes, and require users to re-authenticate.
- Enable users to obtain new access tokens without requiring full re-authentication.
Secure Download Links
Using secure download links is another way to protect files and control access to them. These links ensure that only authorized users can download files.
Here are some ways to generate secure download links:
Generating Secure, Time-Limited Download URLs
Time-limited download URLs provide temporary access to files. These URLs are usually valid for a short period and automatically expire after some time. This minimizes the risk of unauthorized access.
Here’s how you can generate time-limited URLs:
- Generate a URL with an expiration token.
- The server verifies the URL’s validity when a user makes a request.
Code Snippet (AWS)
const AWS = require('aws-sdk');
const s3 = new AWS.S3();
function generatePresignedUrl(bucketName, key, expiresIn = 3600) {
const params = {
Bucket: bucketName,
Key: key,
Expires: expiresIn // URL expires in seconds
};
return s3.getSignedUrl('getObject', params);
}
// Usage
app.get('/download/:filename', (req, res) => {
const filename = req.params.filename;
const url = generatePresignedUrl('your-bucket-name', filename);
res.json({ url });
});
Implementing One-Time Use Links
One-time use links are URLs that can be accessed only once. This ensures that even if the link is shared, no one other than the intended recipient can access the file.
Here’s how you can generate one-time use links
- Create a unique token for each download request and associate it with the file.
- Store tokens in a database with information about their usage and expiration.
- When a request is made, validate the token, check if it has been used before, and mark it as used.
Secure File Storage
Secure file storage ensures that files remain protected even at rest. Here are some ways to ensure secure file storage:
- Use encryption to secure files stored on servers or cloud services. It ensures that data users can only access files and data with a proper decryption key.
- You can implement AES (Advanced Encryption Standard) for symmetric encryption or RSA for asymmetric encryption.
- Encrypt files after they are uploaded to the server.
- Use a secure cloud storage service that implements strong encryption mechanisms.
- Schedule regular backups of your data. It is essential for data integrity and availability in case of data loss or corruption.
- Encrypt backup data to ensure it remains secure.
Secure File Delivery in Enterprise Environments
Here are some effective ways to ensure secure file delivery in enterprise environments:
- Integrate secure file delivery with enterprise identity management systems (IDMs). This enhances access control and streamlines user management. For example, you can integrate file delivery systems with (Single Sign-On) SSO solutions like Active Directory (AD), SAML, or OAuth.
- Implement role-based access control (RBAC).
- Implement multi-factor authentication (MFA).
- Use private networks and VPNs as they provide secure, encrypted connections for accessing enterprise resources. This significantly enhances the security of file delivery systems. For example, you can use a VPN to ensure that file delivery systems are accessible through the corporate VPN. This restricts access to authorized users.
- Use secure gateways or proxies to manage and monitor file access.
- Ensure you comply with relevant data protection and privacy regulations, such as GDPR.
Advanced Security Features
Implementing advanced security features makes the file delivery systems more robust and helps protect files against evolving threats. Here are a few advanced security features to consider:
Implementing Blockchain for File Integrity Verification
Blockchain provides a decentralized system that we can use to verify the integrity of files. By recording file hashes on a blockchain, we can ensure that the files have not been modified since their original upload.
For example, we can create a unique hash for a file using a cryptographic hash function. We can then store the file hashes on a blockchain to prevent tempering.
Zero-Knowledge Encryption Options
Zero-knowledge encryption ensures that data is encrypted in a way that even the encryption provider does not have access to the data. This means only the data owner can decrypt it.
Quantum-Resistant Encryption Considerations
Quantum computers are advanced enough to break current encryption methods. Quantum-resistant encryption protects data against potential quantum attacks.
For example, we can develop cryptographic algorithms specially designed to be secured against quantum computing attacks. Additionally, we can combine traditional encryption with post-quantum algorithms to enhance security.
Conclusion
With cyberattacks increasing day by day, secure file delivery is crucial to protect sensitive information. A secure file delivery system implements robust security mechanisms, such as end-to-end encryption, HTTPS, TLS, access controls, and more. You can build such a file delivery system from scratch or use a secure file transfer solution, such as Filestack. Filestack implements advanced security features to ensure secure file delivery and transfer.
Sign up for Filestack today and implement a highly secure file delivery system!
FAQs
How does Filestack ensure the security of files during transfer and storage?
Filestack uses industry-standard encryption protocols for transfer (TLS) and storage (AES-256). It also utilizes additional security measures like access controls and audit logging.
Can Filestack’s secure file delivery meet compliance requirements like GDPR?
Yes, Filestack complies with GDPR.
How does secure file delivery affect transfer speeds?
While security measures can add some overhead, Filestack optimizes the process to minimize the impact on transfer speeds, especially when used in conjunction with its CDN.
Sidra is an experienced technical writer with a solid understanding of web development, APIs, AI, IoT, and related technologies. She is always eager to learn new skills and technologies.
Read More →